Today, Remote Access is essential in many manufacturing environments for a variety of reasons:
- Physical access may be restricted to technicians or service personnel at times based on internal safety/security reasons or external factors such as the recent COVID-19 pandemic.
- Complicated machines require specialized service and maintenance staff that may not be available on-site.
- Sites may simply be at remote places that are difficult or expensive to access.
- Response time to a critical equipment failure may require immediate action from outside resources.
The challenges to enabling Remote Access are many and require careful assessment of security, usage, and monitoring requirements. The variety of equipment vendors and age adds additional complexity. Many of the systems are old and may not be easily accessed either physically or by a network. Complicating matters is that some of the equipment was supported by resources that have retired. Large OEM equipment comprises complex mechanical and automation systems that sometimes require expert analysis from the system developer. The result is increased costs associated with waiting for a technician to get on-site.
Remote Access in manufacturing plants typically evolves from insular installation to allowing multiple remote support personnel connections. Initially isolated by IT from external access, these connections will require standardization for increased external security while also having connection management for internal equipment and process security. With advances in communications technology brought on by the industrial internet of things (IIoT), connectivity is evolving rapidly.
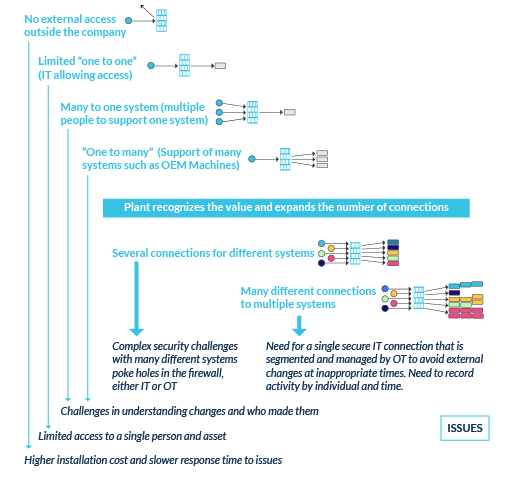
Any strategy requires, at a minimum, addressing three components: (i) where are you now, (ii) where do you want to be, and (iii) how will you get there?
One of the first activities in developing a remote access plan is to assess the current systems being used and the individuals involved. Taking an initial audit will provide a starting point to develop a plan.
The assessment should include the following four areas:
- Technologies and techniques currently being used for Remote Access and assistance
- Individuals both internally and externally involved in Remote Access
- Target devices and assets supported by Remote Access
- Establish an organizational “maturity model” for major categories and your current position
The thought of creating a means for external individuals or companies to gain a connection into the manufacturing plant genuinely concerns IT managers as well as OT managers. Historically, systems had been purposely isolated to protect them from outside interference. Isolation was developed not only from access from outside the plant, but also from other networks inside the business networks that could have an adverse effect on manufacturing operations.
Understanding the differences is an integral part of developing a good relationship between the organizations. These differences are, in some cases, very subtle but it is significant that both sides recognize and understand them. These differences can be in the definition or understanding of common terms. Don’t assume that a word such as real-time has the same meaning in the other organization. Controversy occurs when one side does not fully understand the issues the other side believes are important.
Fish Tank Analogy

An example of the subtle differences can be demonstrated in having two fish tanks, one with salt water and the other with fresh water. If you look at them from the outside, you may consider them to be remarkably similar. However, if you move the fish from one tank to another, the subtle difference will kill them. Knowing the subtle differences is very important when considering the use of IT methodologies in a manufacturing environment.
The development of a Remote Access plan should take into consideration your current state, organizational relationships, and any timing or budget restrictions that can be unique for each company. The guide explores various areas that should be included in a plan with the goal to provide guidance to internal organizations and provide clarity to external companies (OEMs, system integrators, and vendors) so they can offer a more comprehensive solution. The Remote Access Plan should be a controlled document similar to other plans that your organization would have, e.g., a physical access plan.
The following sections cover areas providing you greater insight into your destination and the various methods to reach your goal.
- Creation of an activity classification scheme as well as details or requirements for these activities.
- Identification of equipment or systems referred to as “assets” and the rules and regulations on interactions with them.
- Defining remote methodologies that include various techniques for individual and asset vetting.
- Establishing a security and safety protocol focused on individuals and machines.
- Designing a documentation structure for recording all activities.
architecture
Fundamental to the development of a plan will be understanding the way to communicate with your equipment. This section reviews the communication structures common to devices new or old and the infrastructure required for communication.
Network Segmentation
The need to segment the various devices into many LANs or networks is core regardless of the vendor or type of industrial Ethernet network you deploy. The differences will be mostly on how they will be interconnected. In most cases, there will be a combination of different types of segmentation. A layer 3 switch, often referred to as a router, is the primary method for creating connectivity between LANs.
Non-Routable Ethernet Networks
OEM systems that are isolated machines will typically use a common LAN with the same IP address range to simplify maintenance and support. These internal Ethernet networks cannot be connected to the plant network but are usually interfaced by a computer with one address for internal communication and a second address on the plant network. The use of the computer may not provide a path for Remote Access to reach these devices.
List all your assets even if you currently may only want to have remote connectivity to a subset of them
Some believe that a connection to only higher-level systems such as computers and PLCs will provide the necessary information for remote troubleshooting. In some older systems, the devices below the PLC are connected to older fieldbus networks or vendor-specific remote I/O networks. If this is your current situation, it is still vital to create a list of all assets you can link to, even if it is only possible to do so directly.
There are methods that validate that the individual is the identified resource. All resources accessing systems remotely should be uniquely identified. One must know who was in the system by the individual, not just group access. A continuous validation procedure is essential in which a “multi-factor authentication (MFA)” system is used.
Examples of such process are:

- A user account is created by IT, authenticated by the administrator, account is within a special user-group, Remote Access platform has 2FA, and OT staff can specify the devices the account is whitelisted to access.
- Captive portal or other techniques that makes the user of a public-access network view and interact with a particular webpage before being granted access.
While previous sections have covered the details on the individuals, assets, and methodologies, the remaining sections covers safety and documentation. Creating a centralized location in which individuals can be given timely permission to gain access and document their activity is essential. Not having a centralized approach will lead to ad hoc interactions that may not be captured. This in turn will lead to both security and safety problems.
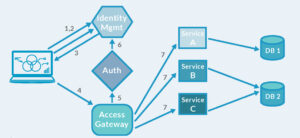
In a well-designed system, identity should not be confused with authorization or access control as they are different functions. They are three different functions. For example, when accessing a VPN concentrator, determining the individual’s authorization should not be the job of the concentrator. Once the identity is confirmed, it should access an authorization service to determine the person’s access rights.
the correct device
Once an individual is verified, the next step is the method to reach the targeted devices. The challenges here are that every manufacturing site typically does not have a uniform environment when it comes to networks and equipment. Most of the differences are not well documented, making it even more difficult. The good news is that the newer systems are better configured with much better documentation. Depending on the location, there may need to be different methods required. Following are four different methods to reach the desired devices:
- Leveraging modern layer 3 switch capabilities
- Cellular connections
- A specialized device to provide connections to target devices or networks
- Creation of a separate Remote Access VLAN
These methods are covered in detail in the Remote Access guide.
While many think that a cyber attack via Remote Access may be more likely than using individuals onsite to support automation systems, it may be the opposite. The level of risk with Remote Access can be lowered due to a greater focus on vetting remote connections and software, while local resources can be infected by creative hackers in numerous ways.
Remote Access may be more secure, if architected adequately, by creating a check before any software or firmware is allowed into the plant.
Validating software prior to use
One area of concern whether the activity is performed locally or from a remote connection is validation that the software is free from any Trojan viruses. Regardless of the activity being remote or local, it is becoming of greater importance that security policies relating to version upgrades and software incorporate vetting before use. Whitelisting software and implementation of security best practices will become more critical to ensure that all software and version upgrades are free from malicious content.
Thechallenges to enabling remote access are many and require careful assesment of security, usage, and monitoring equipment. The variety of equipment vendors and age adds additional complexity. Many of the systems are old and may not be easily accessed either phusically or by a network. Complexity. Many of the sytems are old and may not be easily accessed either physically or by a network. Complicating matters is that some of the equipmenet was supported byt resoucrrces thathave retired. Large OEM equipment comprises complex mechanical and autamation ssytems that sometimes require expert analysis from the system developer. The result is increased costs associated with waiting for a technician to get on-site.
Creating a secure method for Remote Access is important and complex. By documenting the current state of best practices for Remote Access, OMAC has developed a reference point that can be used by OEMs, systems integrators, end-users, and automation suppliers to gauge where they stand with their current or planned Remote Access solutions. The OMAC Remote Access workgroup plans to continue to monitor the technology landscape for Remote Access with the goal of providing ongoing knowledge and experience to the manufacturing industry.
This executive summary is just an outline of the material contained in the 90-page OMAC document, which provides a practical and vendor-neutral outlook with inputs from all individuals involved on either side.
The OMAC “Practical Guide to Remote Access for Plant Equipment” is an essential resource that should be considered by all industry participants who are using or considering to use Remote Access as a part of their plant floor strategy.

